Tutorial that teaches how to use GoogleScraper to scrape 1000 keywords with 10 selenium browsers.
Continue reading
Posted on September 05, 2018 in GoogleScraper • Tagged with tutorial, GoogleScraper, scraping • 3 min read
Tutorial that teaches how to use GoogleScraper to scrape 1000 keywords with 10 selenium browsers.
Posted on August 30, 2018 in Wordpress, WooCommerce, functions.php, CSS, related-products • Tagged with Wordpress, WooCommerce, functions.php, CSS, hide-related-products, disable related products • 2 min read
I found many instructions and guides in the Internet that describe How to hide related products tab on shop page to be NOT WORKING!
It's a freaking pain in the ass to hide your related products tab on your shop page. The method to actually hide related products depends on the WooCommerce theme that you are using. In this article, we are going to present a method that provably works for every theme and WooCommerce version out there.
Step 1. Open the product page where your related products are shown.
Step 2. Right click on the HTML with related products and open page inspect. See the picture below.
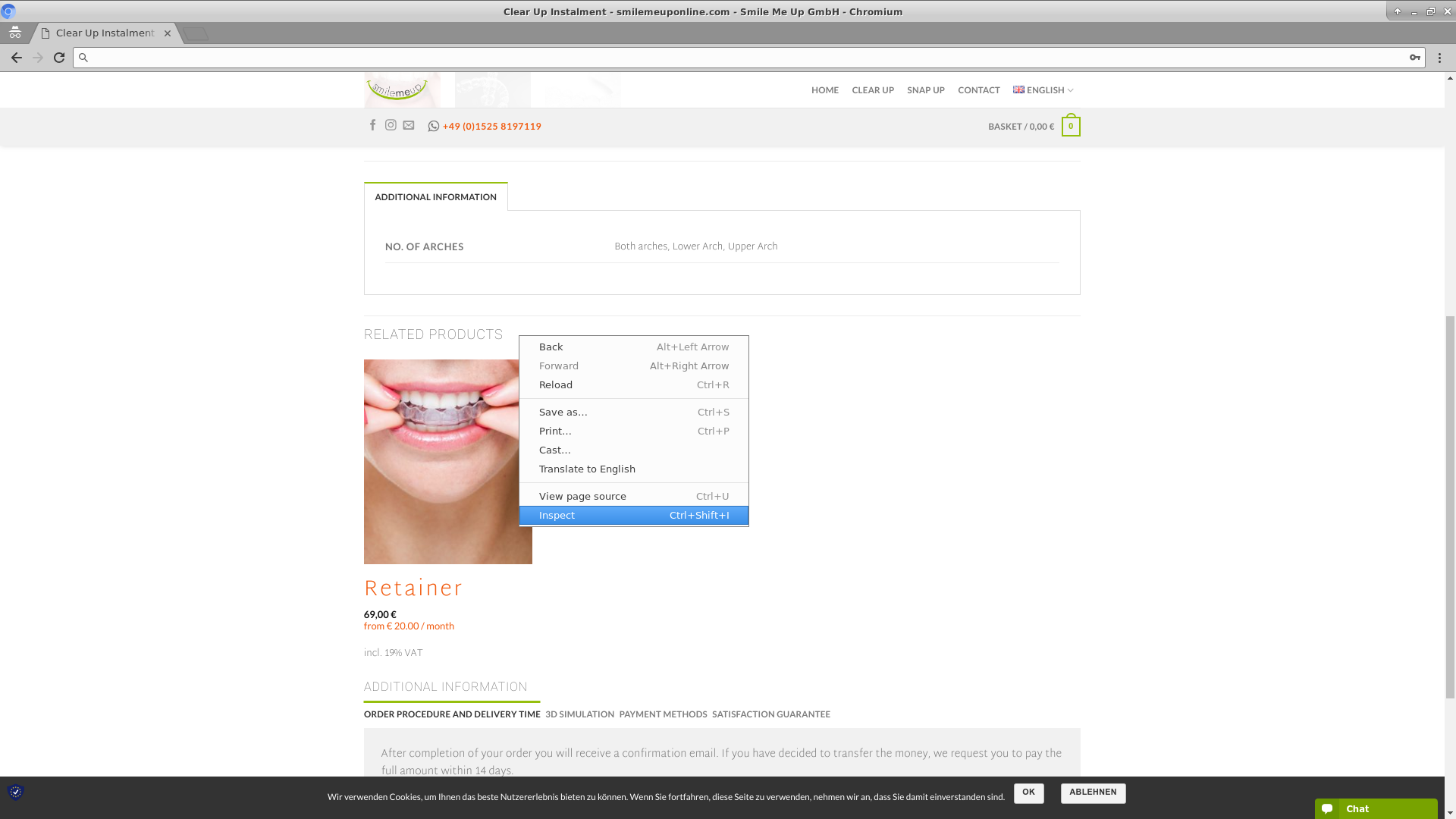
Step 3. Copy the class attribute of the container element that contains the related products HTML.
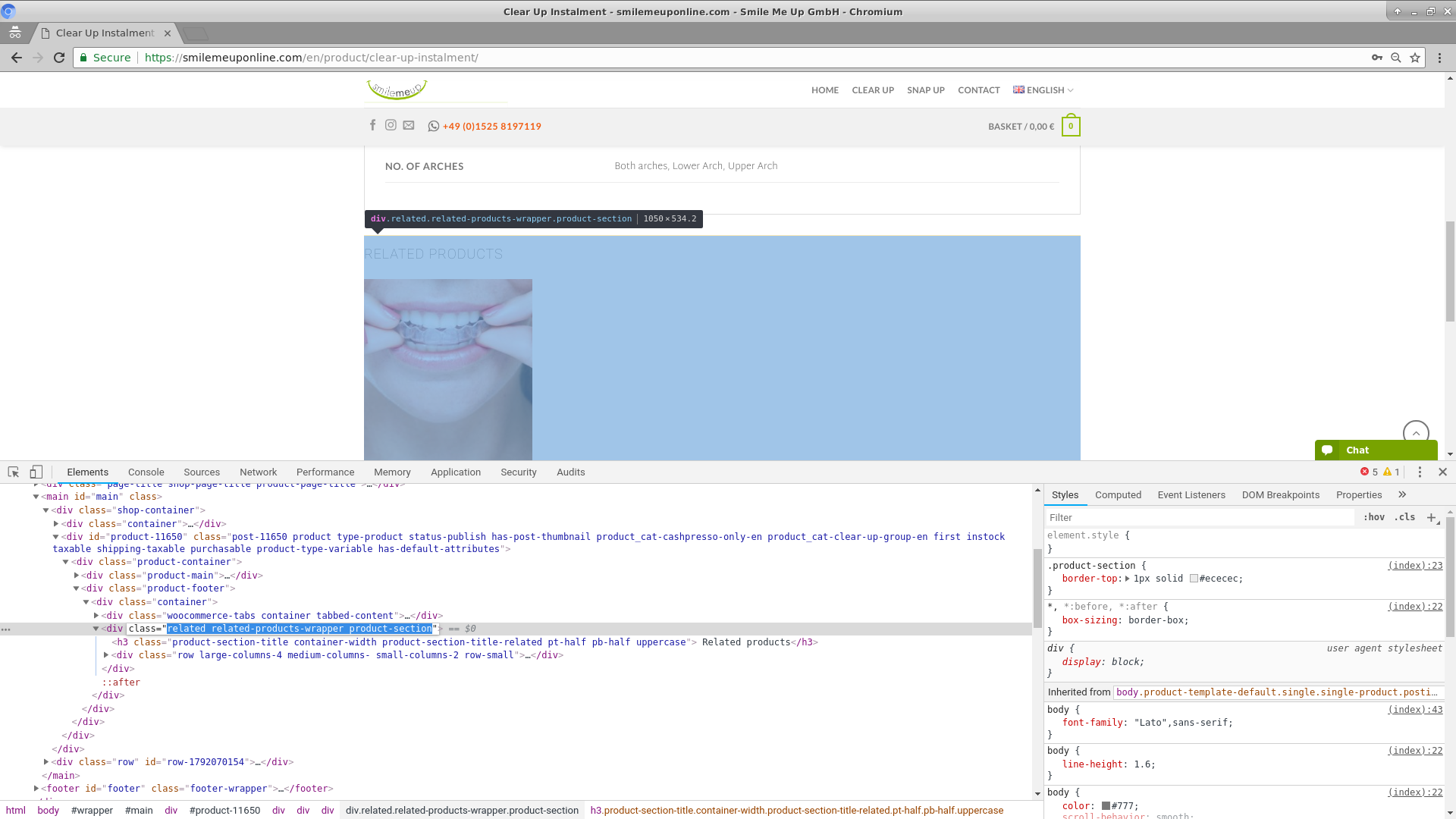
Step 4. Insert the copied class code to this CSS code. In my case, I copied related related-products-wrapper product-section and the resulting CSS will look like this. So you only have to replace spaces ' ' with points '.'.
In my case the final CSS code looks like this:
.related.related-products-wrapper.product-section {
display: none !important;
}
Step 5. Replace CSS code from above with the line {{YOUR CSS CODE HERE …
Posted on August 20, 2018 in Security, Cryptography, MAC, HMAC • Tagged with Math, MAC, HMAC • 6 min read
Similarly as digital signatures, Message Authentication Codes provide message integrity and message authentication. When Alice generates a MAC and sends the message and MAC to Bob, Bob verifies that the message has integrity by calculating the MAC himself. He also authenticates the message, because only Alice could have generated the MAC.
Unlike digital signatures they do however not provide nonrepudiation, since all involved parties share the secret key $k$. MAC's can be implemented using cryptographically secure hash functions (HMAC) or symmetric block ciphers like AES.
A MAC consists of a set of messages $X$, a finite set of hash values $Y$ and a key space $K$. Each key $k$ specifies a hash function $h_k: X \rightarrow Y$. Let $n=|X|$ and $m=|Y|$ and $l=|K|$.
Each MAC must have a property known as computation resistance: Even if an attacker knows $n$ text-hash pairs $(x_n, h_k(x_n))$, it remains computationally unfeasible to find a valid MAC for a message without knowledge of the used key $k$.
The goal of an attacker is to compute a valid MAC for a message $x \in X$ without knowing the secret key $k$. There are a series of different attack categories:
Posted on August 18, 2018 in Security, Cryptography, Hash Functions • Tagged with Math, Integrity, Hash-Functions, Merkle-Damgård • 13 min read
This blog post will introduce cryptographic hash functions. We are going to discuss the Merkle-Damgård construction which underlies many hash functions that were and are used nowadays. The MD4, MD5, SHA-1 and SHA-2 hash families are all functions that built on top of the Merkle-Damgård construction. Then we will introduce an alternative construction that was popularized during the publication of Keccak (SHA-3): The Sponge construction.
But what are cryptographic hash functions good for?
The general idea is to apply a unique and stable fingerprint to each input data $x$. This fingerprint is computed with a hash function $h$ and the resulting value $y = h(x)$ is called a message digest. The size of $h(x)$ is fixed, even though the input data $x$ may have arbitrary length. The intended task for $h$ is to assign a unique identification code $h(x)$ for each input $x \in X$ where $X$ is the set of all possible inputs. The avid reader might realize that this task is impossible, since there is no bijective function that connects an infinite large input set $X$ with fixed sized output set $h(x)$. Thus there must be collisions: For some inputs $x_1 \neq x_2 \in …
Posted on August 12, 2018 in Security, Cryptography • Tagged with Python, Primes, Math, RSA, asymmetric key cryptography, Miller-Rabin Primality Test, Fermat • 11 min read
All sources for this blog post can be found in the Github repository about large primes. The most recent version of the sources may only be found in the Github repository.
It has been a long time since I found the energy to write a new blog post. In this article, I am going to dig into a interesting area of cryptography: The task to find large prime numbers. We hopefully are all familiar with the concept of prime numbers. Prime numbers are integers $p$ which are dividable only by $p$ itself and $1$. But why is it necessary to find large prime numbers in the area of cryptography?
One of the first asymmetric cryptosystems invented was RSA (1977). As all public key algorithms, the security of RSA depends on the existence of a one-way function.
In the case of RSA, the one-way function is built on top of the integer factorization problem: Given two prime numbers $p,q\in \mathbb{N}$, it is straightforward to calculate $n=p \cdot q$, but it is computationally infeasible to reverse this multiplication by finding the factors $p$ and $q$ given the product $n$. Even when the primes $p$ and $q$ are …
Posted on August 10, 2016 in Security • Tagged with Linux, Privilege Escalation, root • 3 min read
This blog post will serve as a cheatsheet to help in my future pentesting experiments and wargames when I am stuck and don't know how to proceed. I hope it will be of use for some people out there. This document will likely change and evolve in future revisions.
In this blog post I will discuss common privilege escalation techniques. I assume that an attack got a foothold into the server by spawning a webshell over SQL-Injections or similar web exploitation vectors.
Other people have published great information about privilege escalation process.
Often you can find login credentials to a custom admin web interface in the database. Because humans tend to reuse the same credentials on different services, it's always worth to check if the discovered login credentials work on other services such as SSH or Telnet. If you can access /etc/passwd, you can try all found credentials on all running services on all user accounts in the passwd file. You may discover …